 Cloud Engineer
Cloud Engineer

mailsforsahan@gmail.com
© 2024 sahan. All Rights Reserved - Website powered by AWS Lightsail
Call Me!AWS Well-Architected - Static Website on AWS


Overview
This document outlines the process followed to deploy a static website hosted on Amazon S3, leveraging other AWS services such as AWS Certificate Manager, CloudFront, and IAM for enhanced performance, security, and compliance with the AWS Well-Architected Framework.
Process and Architecture
1. Creation and Configuration of Amazon S3 Bucket
- Objective: To store and serve static website files (HTML, CSS, JavaScript, images).
- Steps:
- Bucket Creation: Created an S3 bucket named
example-bucketto store website content. - File Upload: Uploaded the static files to the bucket ensuring the structure supports website navigation.
- Bucket Creation: Created an S3 bucket named
- Best Practices:
- Ensured the bucket name was unique across all existing bucket names on Amazon S3.
- Configured the bucket to deny any public access initially until proper policies were put in place.
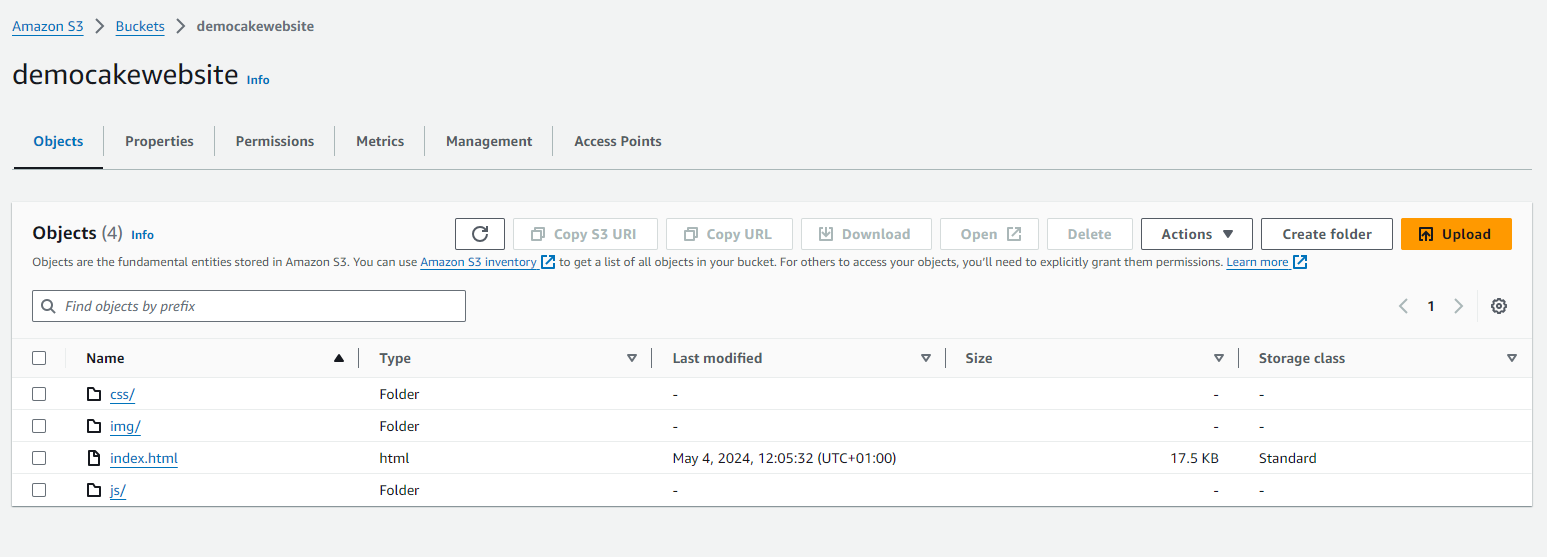
2. Configuring the Bucket for Website Hosting
- Objective: To enable the S3 bucket to function as a static web hosting service.
- Steps:
- Static Website Hosting: Enabled static website hosting in the S3 bucket properties, setting
index.htmlas the index document anderror.htmlas the error document. - Public Access Configuration: Configured the bucket policy to allow public read access to the website files while adhering to the principle of least privilege.
- Static Website Hosting: Enabled static website hosting in the S3 bucket properties, setting
- Best Practices:
- Enabled logging to monitor and record activities for security and troubleshooting purposes.

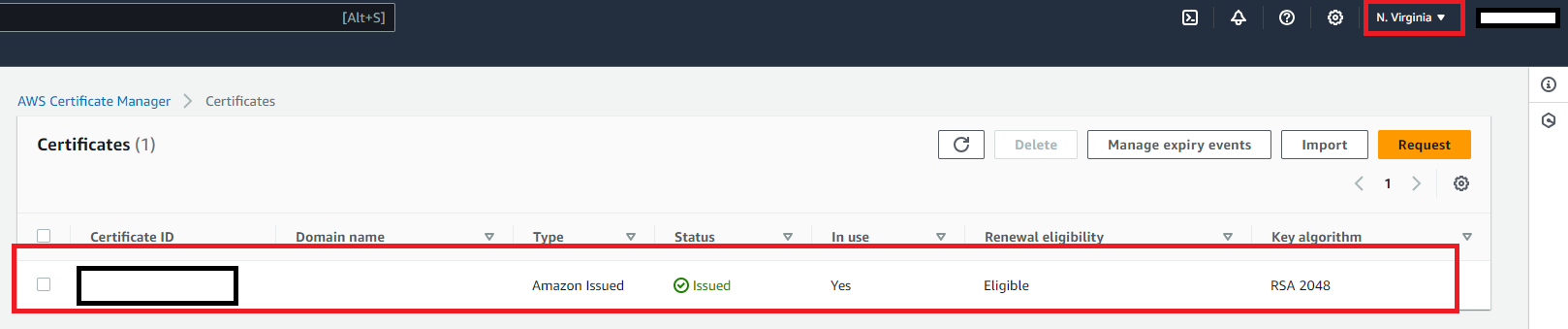
3. Implementation of AWS Certificate Manager
- Objective: To enhance website security by enabling HTTPS.
- Steps:
- Certificate Setup: Requested and verified a public SSL/TLS certificate from AWS Certificate Manager for the domain.
- Best Practices:
- Configured DNS validation for the certificate to automate the renewal process.
- Important:
- Should select US East (N. Virginia)us-east-1 as the location when setting AWS Certificate manager
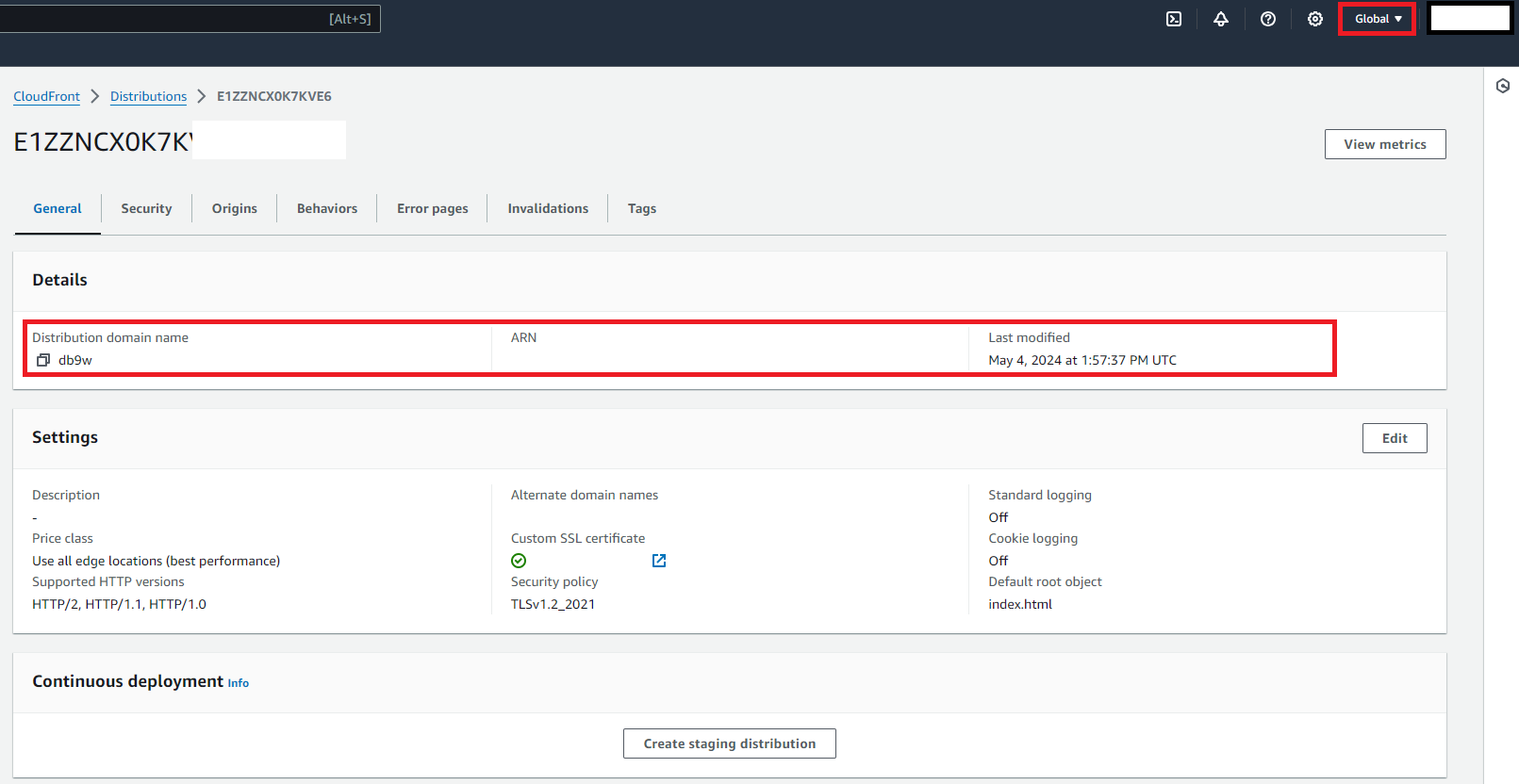
4. Integration with Amazon CloudFront (Global service AWS)
- Objective: To distribute content globally and reduce latency.
- Steps:
- CDN Setup: Created a CloudFront distribution, specifying the S3 bucket as the origin and the ACM certificate for SSL.
- Caching Policies: Configured caching policies and behaviors to optimize delivery.
- Best Practices:
- Used geographic restrictions to manage content distribution based on compliance and business needs.
5. Access Management Using IAM
- Objective: To securely manage access to AWS resources.
- Steps:
- IAM User and Policies: Created an IAM user with permissions restricted to managing S3 bucket contents and administering CloudFront distributions.
- Bucket Policies and IAM Policies: Applied strict bucket and IAM policies to ensure the principle of least privilege, allowing actions only necessary for managing the website content.
- Best Practices:
- Regularly reviewed and refined IAM policies to adapt to changes in the project scope and security requirements.
- admin has access to view the bucket from his IAM account
- Permission was granted by JSON file


S3 Bucket access using admin account
When the admin tries to access different S3 bucket then there will be access denied because of the IAM policies were generated only to access the specific S3 bucket using JSON.

Technologies Used
- Amazon S3
- AWS Certificate Manager
- Amazon CloudFront
- AWS Identity and Access Management (IAM)
Conclusion
The deployment of the static website was aligned with the AWS Well-Architected Framework, focusing on operational excellence, security, reliability, performance efficiency, and cost optimization. By leveraging AWS’s robust cloud infrastructure, we achieved a scalable, secure, and highly available